Phone fraud is one of the most common forms of digital deception. Spoofing by fraudsters, where a fake number mimicking contacts from banks, support services, or government agencies is displayed on the phone screen, poses a particular danger. This creates a complete illusion of authenticity for the victim.
Such an approach gives criminals a real advantage. The victim loses vigilance and is ready to engage in dialogue. As a result of conversations, attackers gain access to bank card data, accounts, or even remotely control the device. Such schemes use psychological pressure and cause anxiety to achieve quick results.
Why a fake number looks real
Number spoofing by fraudsters is carried out through IP telephony (VoIP), which allows manually setting the number displayed to the interlocutor. This technology is legally used in call centers but is also available to criminals. Thus, they can call from any numbers, including those similar to real phone numbers of banks or telecom operators.

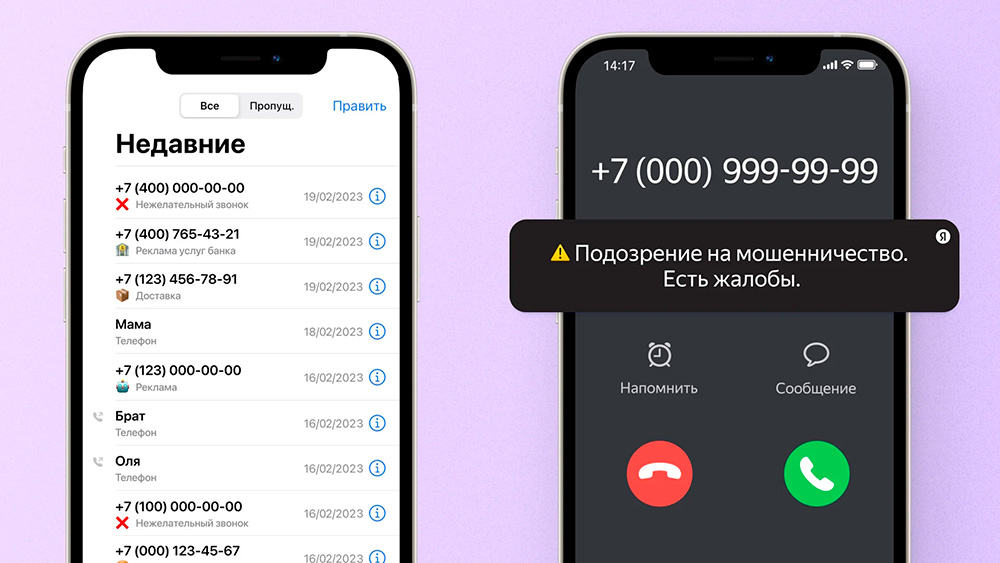
On the phone screen, the user sees a familiar or visually official number. Sometimes the name of an organization is used if it is saved in contacts or has previously been displayed. In such a case, the fraudulent call enters the same call history as genuine ones. This allows creating an illusion of authenticity. As a result, call security is compromised even before the victim answers. Checking the authenticity of a number independently is almost impossible, which criminals actively exploit.
How attackers operate: a typical scenario
The main goal is to make the user believe they are speaking with a bank or security service representative. The conversation often begins with an alarming message (suspicious transactions detected, someone is trying to get a loan, or the card will be blocked). All this is part of a pre-built social engineering scheme.
Criminals speak calmly, confidently, using technical terms. If the victim starts to doubt, a “senior specialist” is involved—an additional interlocutor, allegedly from another department. This enhances credibility and strengthens trust. They demand quick identity confirmation to “protect the account,” and under this pretext, obtain confidential information.

Some schemes include sending links to fake websites or applications. Fraudsters ask to install them “for funds protection,” but in reality, gain access to device control. Such phone fraud is increasingly applied comprehensively (call + SMS + fake site).
How to identify a fraudulent call
The most dangerous feature of such calls is visual credibility. However, there are several signs to watch out for. First of all, real organizations never request SMS confirmation codes, logins and passwords, passport data, or card numbers over the phone. If the conversation involves urgency, threats of blocking, or overly insistent recommendations—it is a clear sign of deception. To reduce risk, it is recommended to:
- not provide personal or payment information over the phone;
- end the conversation immediately if pressured or threatened;
- call back the number listed on the company's official website;
- install antivirus applications;
- report the incident to the operator or bank.

It is also necessary to be cautious if the interlocutor gets confused in terms, cannot clearly explain the situation, or gets irritated with clarifying questions. All these actions help ensure the protection of personal data and prevent falling victim to manipulations.
How to enhance security: technical and behavioral measures
Technology certainly helps in the fight against fraudsters. Some operators have long been blocking numbers noticed in spoofing. Mobile applications have also appeared, capable of alerting about fraud risks or automatically rejecting suspicious calls.
However, the technical component alone is not enough—it is important to develop digital awareness. Installed applications should have limited permissions, not access call logs, SMS, or contacts. Regular operating system updates help close vulnerabilities exploited by criminals.
It is also necessary to remain vigilant even with incoming calls from familiar numbers. If there is the slightest doubt, it is better not to continue the dialogue. Genuine organization representatives will not insistently demand immediate responses. Call security is not only about technology but also user behavior. The higher the level of awareness, the fewer chances fraudsters have to use number spoofing.
 >
>