Modern accounts are not just a way to stay connected. They are often linked to work chats, advertising accounts, and banking connections. Therefore, hacking a social media account is not just about stealing photos or conversations. Most account thefts do not happen accidentally. Intruders use already known gaps in security. Let's look at why accounts are hacked and how to protect yourself from unpleasant consequences.
Why Accounts Are Hacked
Most social media hacks pursue specific benefits. Intruders rarely act “just because.” The goal is to use the account as a tool. After capturing the page, it begins to turn into a platform for deception, mailings, or making a profit in other ways.
If it is a personal profile, it is used to send links to phishing sites, requests to “lend money,” or participate in fake promotions. People receiving a message from a friend tend to react without further verification. This builds a chain attack scheme — one hack leads to others.

Through conversations, documents, and linked email, one can access banking accounts, cloud storage, or other services, especially if the same passwords are used everywhere. Business accounts and profiles with an audience are interesting because of their monetization. They post paid posts with fraudulent content, reconfigure advertising accounts, and steal client bases. Sometimes such pages are resold in shadow chats for a fixed amount.
In some cases, the account is held under threat. Scammers demand a ransom for return, blackmail with the publication of personal data or intimate correspondence. This is rare, but it shows how serious the consequences can be.
Each hack creates a chain of similar hacker attacks. That is why even an apparently “empty” page needs protection no less than an account with thousands of followers.
How Scammers Operate – The Entire Scheme in Detail
One of the most common ways to hack is phishing. The user receives a message with frightening content:
- suspicious activity;
- profile freeze;
- access confirmation.
Inside such a mailing is a link to a fake login page that is 90% similar to the official site. The person enters a login and password, not noticing the trick. All this immediately falls into the hands of intruders. As soon as the data is entered, it is with the hacker. Then follows the standard procedure, namely changing the password, disabling two-factor protection, deleting the email, and phone number.
The second method is through external services. Some applications under the guise of “Instagram analytics” or “automatic posting” require authorization. At the same time, the data goes directly to third parties. Often such applications are created specifically for specific waves of attacks.
Also common is the scheme through an already hacked account. The user receives a link supposedly from a friend and, unsuspectingly, becomes a victim themselves. Some mailings come from brand pages that have already been hacked.
Signs of Unauthorized Interference
Sometimes the capture happens quietly. The hacker does not immediately change the login and password but waits for the right moment. But there are signs to watch out for immediately.
The first is logins from unfamiliar devices or regions. Most social networks send notifications about new sessions. The second is suspicious actions: likes, subscriptions, stories that were not published by the owner. Sometimes these are direct mailings to subscribers — with a request to send money or follow a link.
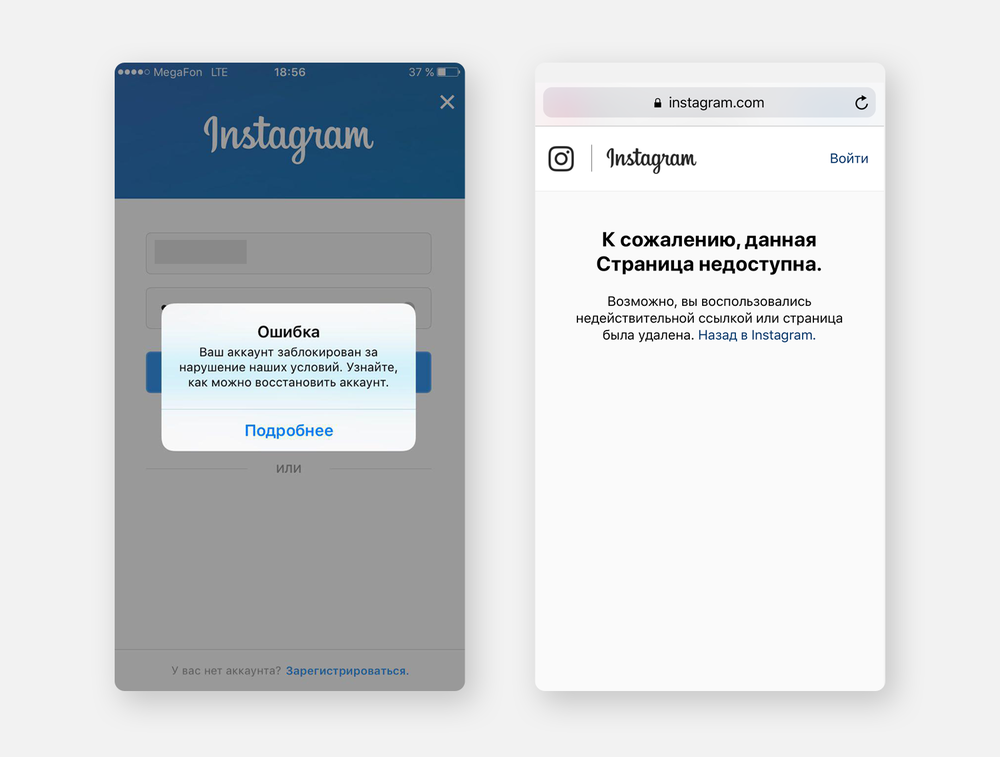
If the message “wrong password” appears, and the email and phone are no longer linked — the hack has already occurred. In this case, urgent recovery is required, otherwise access may be lost to connected pages or advertising accounts.

What to Do If Instagram Is Already Hacked
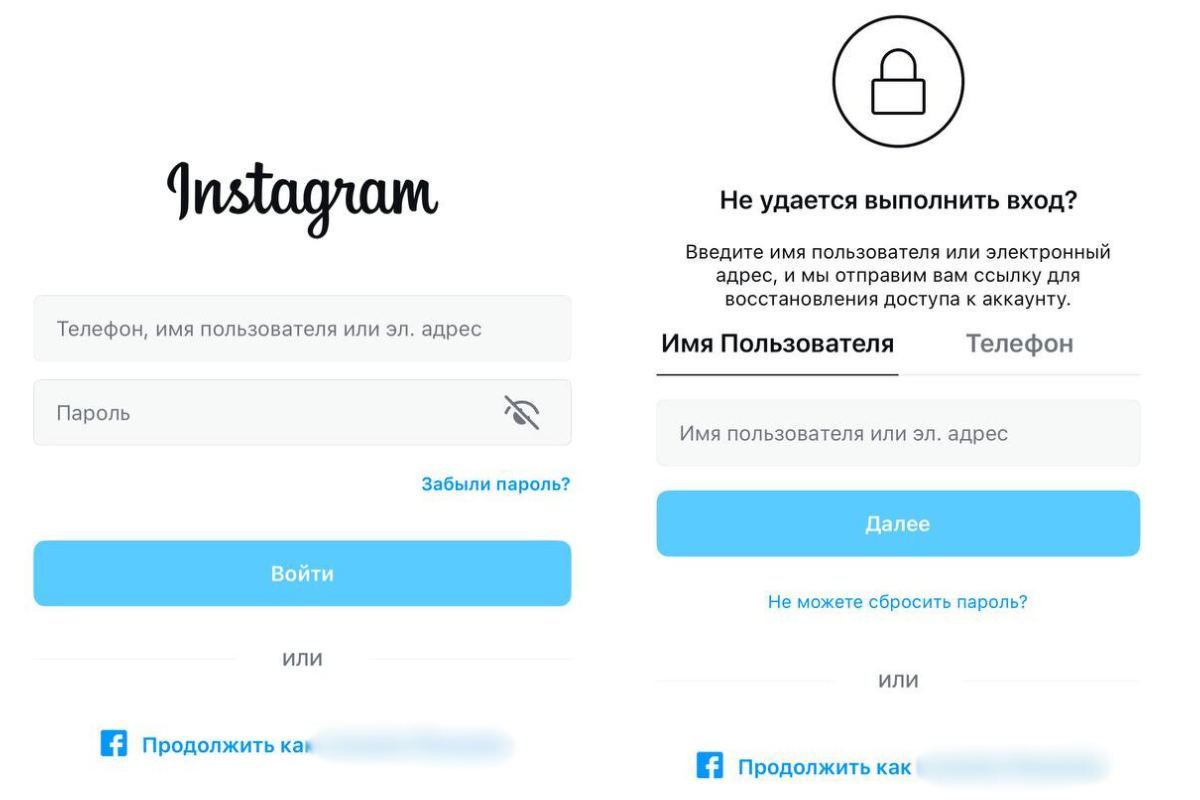
Instagram is one of the social networks that scammers most often try to access. If the account login suddenly disappears, do not delay — proceed to recovery immediately. Even if the email or number has already been changed, the system may still “recognize” the old data. The main thing is to go through the entire process step by step, without rushing:
- open the login page and click “Forgot Password?” or “Need help logging in?”;
- enter your old username, email, or number that were linked to the account;
- click “No access to these data” to open additional recovery methods;
- provide a backup contact and upload a photo to confirm identity;
- wait for a response from support and follow the recovery instructions.
After verification, Instagram sends a link to change the password. If all the data matches, access is restored. The restored profile should be immediately protected — change the password and enable two-factor authentication.
Social media hacking is an unpleasant experience. It is important to learn to respond quickly to “intrusions” in order to protect your data and personal information.
 >
>